Manufacturing Cyber Security


The fast-paced digitalization of manufacturing workflows increases the chance of cyber security threats. As per the research conducted by Deloitte, 40% of stakeholders reported having cyber security incidents during the last 12 months.
The foremost cybersecurity incidents faced by businesses in the manufacturing industry include:
- Unauthorized access
- Intellectual property theft
- Operational disruption
- Safety system incidents
- Compromised product quality
Manufacturing Cyber Security Breaches: Real-world Cases
Manufacturing companies worldwide get hacked, losing millions of dollars caused by production disruptions and recovery activities.
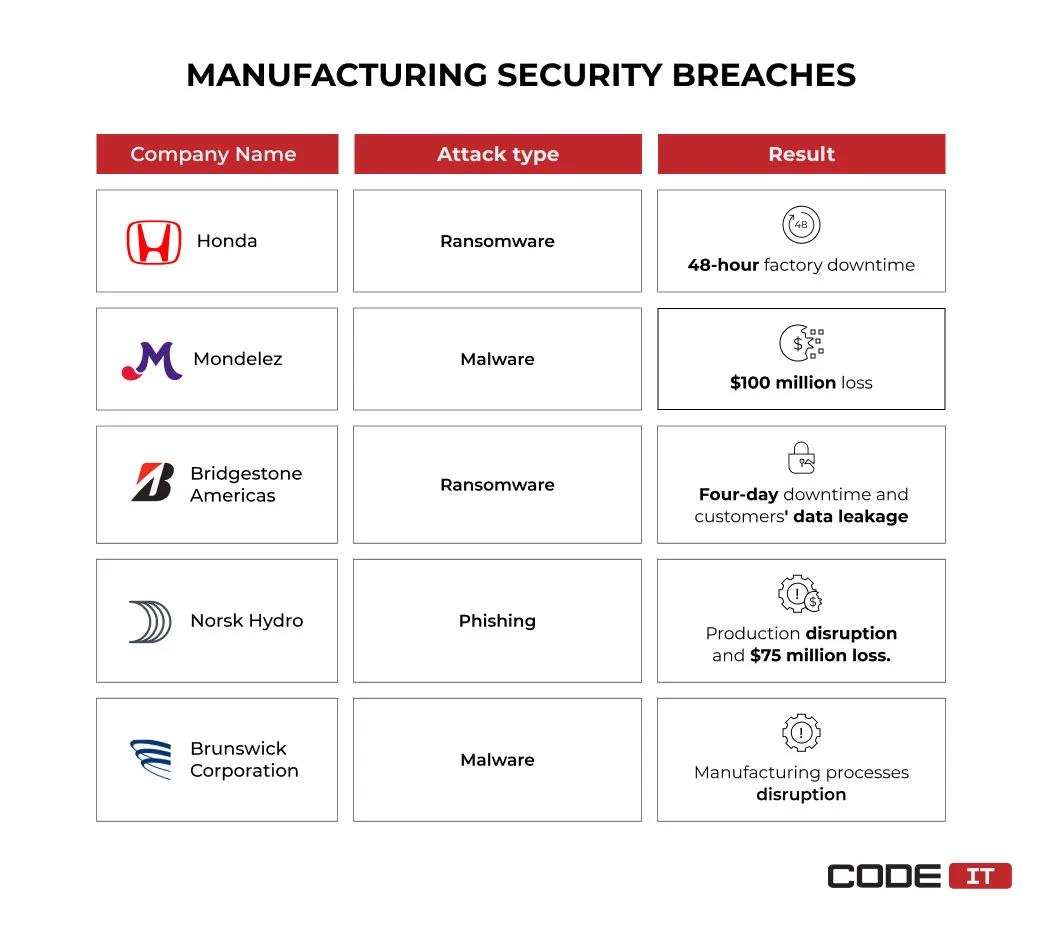
1. Honda
WannaCry, a self-copying malware, has broken into the Honda’s plant located in Tokyo. It has disrupted the production process with a DDoS attack. The malware has exploited the security loopholes discovered in an unpatched version of Windows OS.
Result: The factory went down for 48 hours, halting the production of more than 1,000 vehicles.
2. Mondelez
The NotPetya malware has intruded the system using a phishing email. It has tricked a user into obtaining admin permissions. The malware has encrypted the master file table and demanded a Bitcoin ransom to regain access to the files.
Result: The intellectual property theft in manufacturing and user credentials resulted in a $100 million meltdown.
3. Bridgestone Americas
Hackers have exploited loopholes in outdated software to break into the internal network and update remote desktop access (RDP) configurations. The deployed ransomware has shut down manufacturing networks.
Result: Exposed customers’ data and production downtime that lasted for days until the company completely recovered from the attack.
Order security audit to check your software
Business First
Code Next
Let’s talk
4. Norsk Hydro
Hackers have shut down the production processes and critical equipment by forcing unauthorized password changes and disconnecting computers from the network. The hackers gained access to the company’s system by using compromised access credentials.
Result: The failed manufacturing cyber security caused a $75 million loss because of production disruptions and recovery activities.
5. Brunswick Corporation
A trojan attached to a phishing email has broken into the company’s system. It has bypassed detection mechanisms and appeared legitimate using the stolen credentials.
Result: A nine-day factory downtime and costly recovering activities.
Manufacturing Cyber Attack Goals + Business Impact
The three major goals of cyber attacks on a manufacturing infrastructure are as follows.
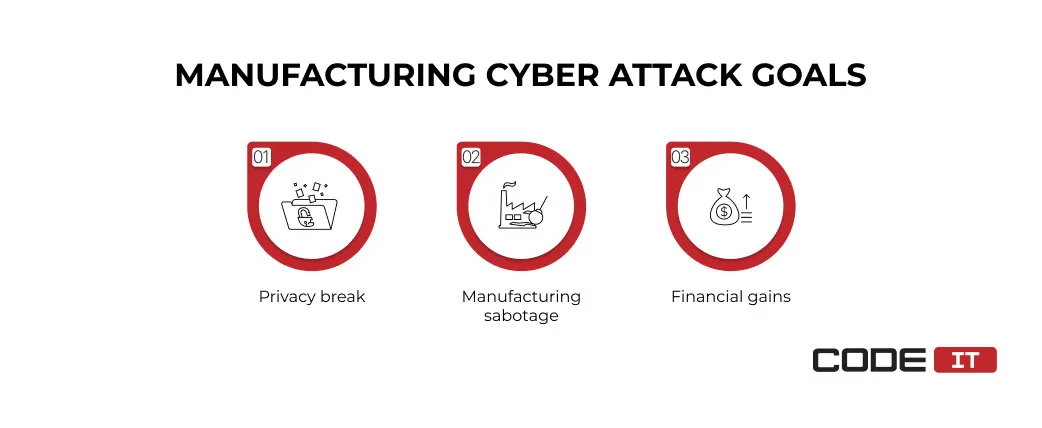
1. Privacy Break
A break into secured systems to access administrative files, research findings, etc. Also, hackers may get access to the authentic product design for counterfeiting purposes.
Business impact: Reputation damage, competitive advantage loss, and violation of commercial agreements.
2. Manufacturing Sabotage
Illegal activities aimed to stop production by damaging machines, changing workflows, introducing defects, failing software solutions, etc.
Business impact: Damage of machines, product quality degradation, violation of safety regulations, defective product recall.
3. Financial Gain
The external software/hardware block aimed to get ransom payments for unblocking the critical functionality.
Business impact: Unplanned operational downtime, loss of money, new security infrastructure investments.
Looking for expert help? Check
Manufacturing Targets And Vulnerabilities
The foremost targets of manufacturing cyber security breaches are:
- Manufacturing machines. Physical equipment used for producing items, assembling products, etc.
- Sensors and actuators. The infrastructure of Internet of Things (IoT) devices is used to measure conditions/physical properties and perform programmed tasks.
- Programmable logic controllers (PLCs). Processing nodes are designed to issue commands to machines.
- CAD software. This software helps design items. The altered settings may lead to the generation of incorrect or damaged files by the design team.
- Stereolithography. STL files are widely used by manufacturers for storing information about the surface geometry of a 3D object.
- G-code files. The files that are used for programming PLCs. They help define processing parameters and store crucial item design information.
Areas usually define the architecture of cyber security for advanced manufacturing. Hence, let’s check the core vulnerabilities in a plant floor by area.
1. Hardware and software
- Machines/programs run for days without checks or security updates.
- Multiple ways for inputting instructions (e.g. laptops, USB sticks, integrated systems).
- Legacy equipment and software with insufficient security features or undocumented loopholes.
2. Networking
- No isolation between the different networks.
- Not encrypted wired and WiFi connections.
- The HTTP protocol usage by business applications.
3. Internal
- Absence of security policies.
- Computers left unlocked by employees.
- Security rules are not followed/ignored by workers.
- Installation of unlicensed/hacked programs.
- Data transfer from and to unauthorized sources.
Attack Types And Countermeasures
The purpose of implementing cyber security in the manufacturing industry is to keep internal systems safe from external threats.
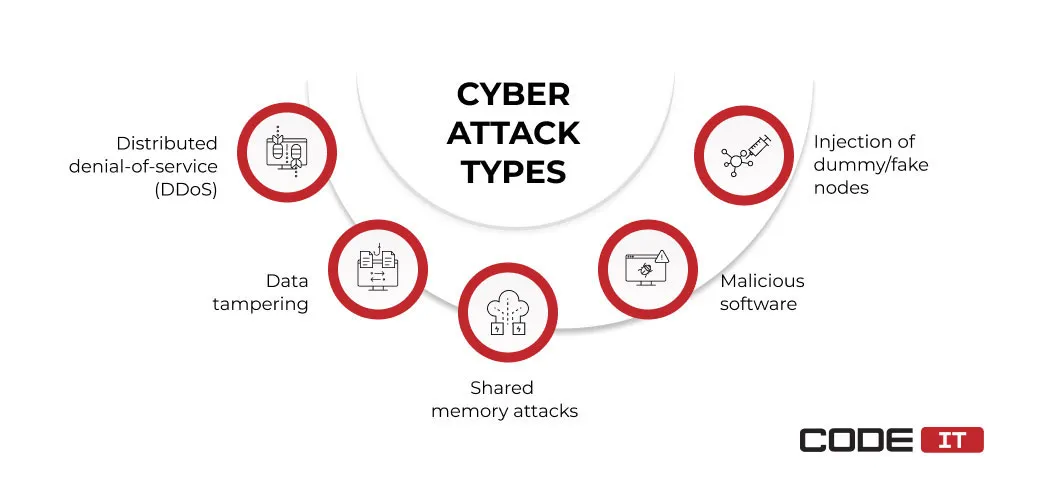
The top types of attacks and countermeasures are:
1. Distributed Denial-of-Service (DDoS)
The process of overloading a system or network with an overwhelming amount of traffic that it cannot handle. DDoS attacks aim to shut down a system entirely or slow it down, causing disruptions in production or unplanned downtime.
Countermeasures:
- Firewall/gateway and proxy
- Secure communication (VPN, WiFi, IP)
2. Data Tampering
Data tampering describes unauthorized access to data and its alteration. Hackers can change machine programs, parameters, and other details. Manufacturing data can also be intentionally destroyed or encrypted.
Countermeasures:
- Encryption of communication
- Encryption of stored data (digital signature)
- Access control/multiple authorizations
3. Malicious Software
A harmful software designed to infiltrate an internal network and systems. An enterprise’s software can be infected by malware to disrupt production processes and access unauthorized data. Also, malware may be designed to use an enterprise’s infrastructure for secretly spreading using connected networks to infect as many systems as possible silently.
Countermeasures:
- Antivirus and malware protection
- Software updates
- Firewall/gateway and proxy
4. Injection of Dummy/Fake Nodes
The exploit of data validation loopholes in a system caused the poor cyber security in manufacturing architecture design. It enables the opportunity to issue unauthorized commands to PLCs or data management systems that will be recognized as legitimate commands from authorized users.
Countermeasures:
- Access control/multiple authorizations
- Encryption of communication
- Encryption of data streams
5. Shared Memory Attacks
The practice exploits the vulnerabilities of systems that use shared repositories. Usually, the attack type succeeds only when exploiting poor access controls or sanitization practices.
Countermeasures:
- Access control/multiple authorization
- Encryption of communication
Not all countermeasures are implemented? Order security audit!

Business First
Code Next
Let’s talk
Cybersecurity Guidelines For Factories
Implementing best practices in the manufacturing industry’s cybersecurity includes various technical and organizational activities.
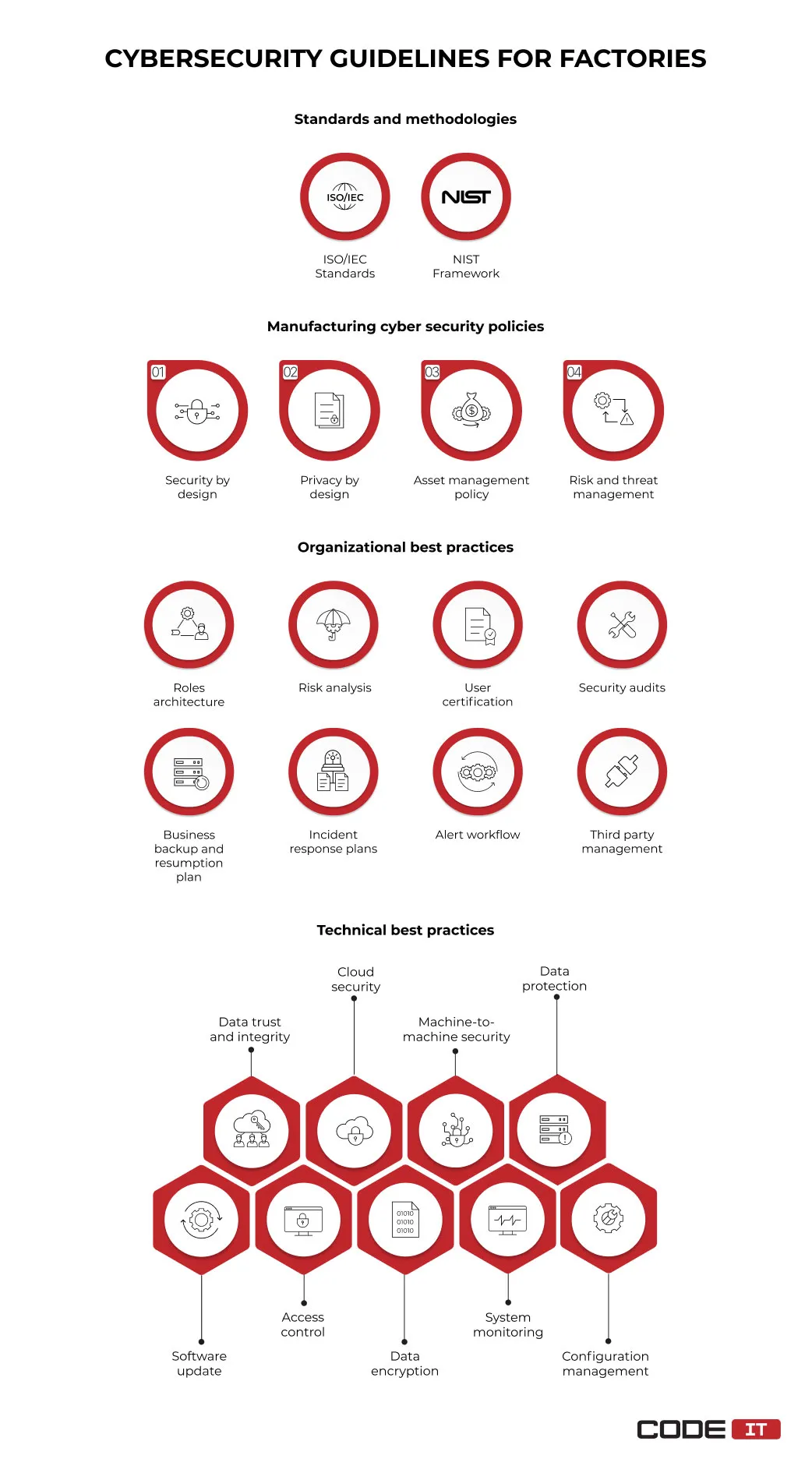
1. Standards and Methodologies
Adherence to defined standards helps improve the overall level of safety from cyber security threats in the manufacturing industry. They provide rules for securing industrial systems and networks.
1.1. ISO/IEC Standards
The cyber security recommendations from the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) are the most widely applied in the manufacturing industry.
The two most popular standards that help withstand cyber security threats in manufacturing and Industry 4.0 are:
- ISO/IEC 27002. A checklist of cyber security manufacturing best practices. Lacks security recommendations for cloud-based systems.
- ISO/IEC 27017. A set of rules for cloud providers and users aimed to make cloud-based environments more secure against manufacturing cyber security risks.
1.2. NIST Framework
The National Institute of Standards and Technology (NIST) has designed a framework for addressing cyber security risks in industrial control systems.
It presents standards, guidelines, and practices that help enable secure communication of cybersecurity activities. Implementing the framework requires an enterprise to have defined coordination among its organizational levels.
2. Manufacturing Cyber Security Policies
The usage of policies and procedures helps ensure new solutions are designed and maintained with cyber security for manufacturing in mind. The top four policies to create and follow are:
- Security by design. A set of measures that should be applied in the early stages of software architecture design and development.
- Privacy by design. A checklist of rules aimed at protecting users’ personal data and compliance with data protection regulations.
- Asset management policy. The measures focused on defining asset management tools. The rules are also dedicated to maintaining a dedicated management network.
- Risk and threat management. Recommendations to addressing manufacturing cybersecurity risks.
3. Organizational Best Practices
The list of organizational rules and responsibilities helps guide employees in maintaining a high level of awareness and ensuring cyber security protection.
3.1. Roles architecture
All roles and responsibilities should be clearly defined according to business goals. This enables the development of a secure communication plan and access risks for each role separately.
3.2. Risk analysis
Classify and prioritize security objectives. Hire a certified vendor to assess an IT system’s manufacturing cybersecurity risks and security measures. The NIST framework comprises a set of practical instructions for running risk assessments.
3.3. User certification
The diversity of user training approaches ranges from occasional workshops to detailed learning programs. This best practice aims to increase workers’ awareness about existing security threats and countermeasures. It’s recommended that educational materials and detailed policies be developed.
3.4. Security audits
Regular audits help ensure the security of an IT system does not comprise unpatched vulnerabilities. The core components are security mechanisms check and threat scenarios simulation.
3.5. Business backup and resumption plan
Large enterprises take days to recover after cyber security incidents if they refuse to pay a ransom. Hence, having a step-by-step response plan is a good practice that helps limit losses caused by an attack. It’s advisable to create different response plans depending on threat types and sensitive data backup strategies.
3.6. Incident response plans
The uncertainty of a high level usually occurs when manufacturing cyber security breaches happen. Therefore, it’s recommended that detailed plans be developed that employees need to follow to respond to limit the negative impact of a security breach. Also, an incident response plan guides employees on operating a factory manually when an automated IT system stops because of an incident.
3.7. Alert workflow
The defined alert management systems help employees to report incidents rapidly. The workflow answers the following questions:
- Who should I alert about incidents?
- Who is responsible for coordinating actions?
- What initial measures should be applied?
3.8. Third party management
The poor management of integrated software solutions has caused the attack on Applied Materials. Therefore, it’s required to manage third-party integrations, following the following recommendations thoroughly:
- Enables strict access control for manufacturing extensions
- Set the minimum required privileges
- Omit direct connections of third parties to the control or production layer
Manufacturing Visibility: Real-Time Insights and Analytics
4. Technical Best Practices
The implication of appropriate technical measures helps protect the physical manufacturing environment from cyber breaches. The following best practices will help secure IoT-driven and smart plant floors.
4.1. Data trust and integrity
Ensuring data trust and integrity helps limit the opportunities for malware to break into a system. The core steps to implement this best practice include:
- Verify data sources before connecting them
- Authorize IoT devices connected to a plant’s network
- Define secure communication channels
- Implement data encoding/decoding mechanisms
- Monitor data in transit and at rest for detecting unauthorized access
4.2. Cloud security
The security of a cloud infrastructure is crucial for keeping smart plant floors safe from cyber attacks. The cloud security recommendations are:
- Choose the best cloud provider
- Request implementing additional security measures from a cloud provider
- Implement decentralized cloud storage to avoid a single point of failure
- Identify critical systems installed on a cloud infrastructure
- Encrypt data when transferring it from/to a cloud
4.3. Machine-to-machine security
Implement comprehensive security measures for machine-to-machine communication, including the following:
- Implement a hardware security module to safely store digital keys
- Apply diverse encryption algorithms to different entities
- Develop communication protocols capable of identifying unusual activities
- Implement white list input validation to protect an IT system from cross-site scripting and command injection attacks
4.4. Data protection
The technical aspect of this manufacturing cyber security best practice defines the confidentiality of data when it is transferred across different levels of an organization. The implementation of data protection activities needs you to:
- Categorize data sets by leakage risk and importance
- Grant data access with the least privilege
- Set expiration for data access
- Document configuration change
- Anonymize personal data when sharing it with other systems
4.5. Software update
Unpatched security loopholes are frequently exploited by hackers to intrude into the IT systems of manufacturing companies. Strict software update policies help ensure no altered software is installed. The recommendations include:
- Double-check the source for downloading new software releases
- Deploy security patches incrementally to ensure it doesn’t lead to negative outcomes
- Additional security measures should be applied if unpatched loopholes have been discovered
4.6. Access control
Advanced control measures should be applied to IoT devices because they can be accessed and controlled remotely. The best practice’s core aspects are:
- Authentication and authorization for IoT devices
- Multi-factor authentication implementation
- Dedication to the least privilege application
- Automated account lockout
- Segregation of networks with remote access
Industrial IoT For Manufacturing
4.7. Data encryption
Everything is connected to Industry 4.0 plant floors. Hence, it’s crucial to develop secured and reliable networks, applying the following recommendations:
- Use secure communication protocols and encrypt data
- Ensure interoperability between different protocols
- Disable unused services
- Stick to using a limited variety of protocols
4.8. System monitoring
The thorough review of logs, network traffic, and other activity helps identify suspicious activity and possible security breaches. The following activities help conduct cyber security monitoring in manufacturing:
- Real-time log monitoring using a Security Information and Event Management (SIEM) system
- Manual review of logs and data access privileges
- IoT device uptime monitoring in real time
- Implementation of a passive monitoring solution
4.9. Configuration management
IoT-enabled systems comprise a lot of smart devices with diverse configurations. Therefore, it’s advisable to check devices’ configuration and backups. The security measures of this best practice include:
- Define the default security configuration for each IoT device
- Thoroughly document any changes in device configuration
- Install configuration management tools to automate workflows
- Backup the latest security configuration settings for each device
Build a secure IT system

Business First
Code Next
Let’s talk
Cyber Security Trends In Manufacturing
As per statistics, the manufacturing industry is the most attacked industry by hackers. More than a ¼ of all the attacks are accountable for the manufacturing—mostly, because they tend to pay ransom.
6 out of 10 manufacturers report an increased number of cyber attacks.
Ransomware is the fastest-growing attack type, with a 3.5-fold increase in the last few years. Hence, 66% of organizations reported being targeted by ransomware. The industry average recovery cost from ransomware attacks in manufacturing is $4.54 million per one.
83% of manufacturers consider their IT systems secured.
As per industry stakeholders, the major cybersecurity threats for manufacturers are as follows:
- 87% — unauthorized access
- 86% — operational disruption
- 85% — intellectual property theft
The top five trends in manufacturing cybersecurity implementation include the following:
- Zero trust security architecture
- AI-driven analysis and threat detection
- Security for industrial IoT (IIoT) devices
- Regulatory compliance
- Ransomware and cyber hygiene
Final Words
The implemention of manufacturing security requires organizations to incorporate a wide variety of activities to keep their plant floors safe from threats.
The foremost types of attack include:
- Distributed denial-of-service
- Data tampering
- Malicious software
- Injection of fake nodes
- Shared memory attacks
The four types of countermeasures are:
- Security standards and methodologies implementation
- Manufacturing cyber security policies creation
- Organizational best practices for security
- Technical best practices for security
FAQ
The manufacturing industry cyber security defines a set of measures that help protect IT systems from threats. The measures include both operational and technical activities.
Ransomware is the #1 type of cyberattack targeting manufacturers. The other popular attack types are:
- Unauthorized access
- Distributed denial of service (DDoS)
- Intellectual property theft
The NIST framework comprises a set of guidelines that help identify cybersecurity risks. Also, the framework helps apply countermeasures to safeguard a plant floor from threats and recover fast in case of data breaches in manufacturing.
The top organizational manufacturing cyber security best practices include the following:
- Roles architecture
- Risk analysis
- User certification
- Security audits
- Business backup and resumption plans
- Incident response plans
- Alert workflow
- Third party tools management
The recommended steps for securing IT systems from cyber security threats in the manufacturing industry include:
- Data trust and integrity mechanisms implementation
- Enhanced cloud security
- Machine-to-machine security
- Data protection measures
- On-time software update
- Thorough access control
- Data encryption
- System monitoring
- Security configuration management
Define the roles and identify the foremost risks. This helps adjust learning materials for employees with different responsibilities. Then, conduct a workshop or prepare learning materials on possible threats and how to avoid them.
Also, it’s recommended that alert workflows and emergency response plans be created so that employees have defined guidelines to follow when an incident occurs.
Build your ideal
software today