Cybersecurity in healthcare: how to counter today’s threats?

The problem of cybersecurity and, consequently, cybercrime has long ceased to be the subject of discussion and concern of some narrow circle of specialists. Today, given the insane pace of the world’s digitalization, the issue of protection in digital space is causing serious debate at the highest level.
As you know, the process of digitalization and digital transformation affects all industries and market segments. Of course, these changes touch on the healthcare industry too. The specificity that is inherent in this industry, namely, concerns for the patients’ health and the storage and dissemination of their personal sensitive data, determines the appropriate attitude towards cybersecurity. Perhaps there is no other industry where cybersecurity has caused such serious concerns and focused attention.
We invite you to join our discussion on the state of cybersecurity in healthcare as of 2021, what measures are being taken to strengthen it, and what steps you can take to increase the security of your healthcare software products right now.
Disturbing statistics
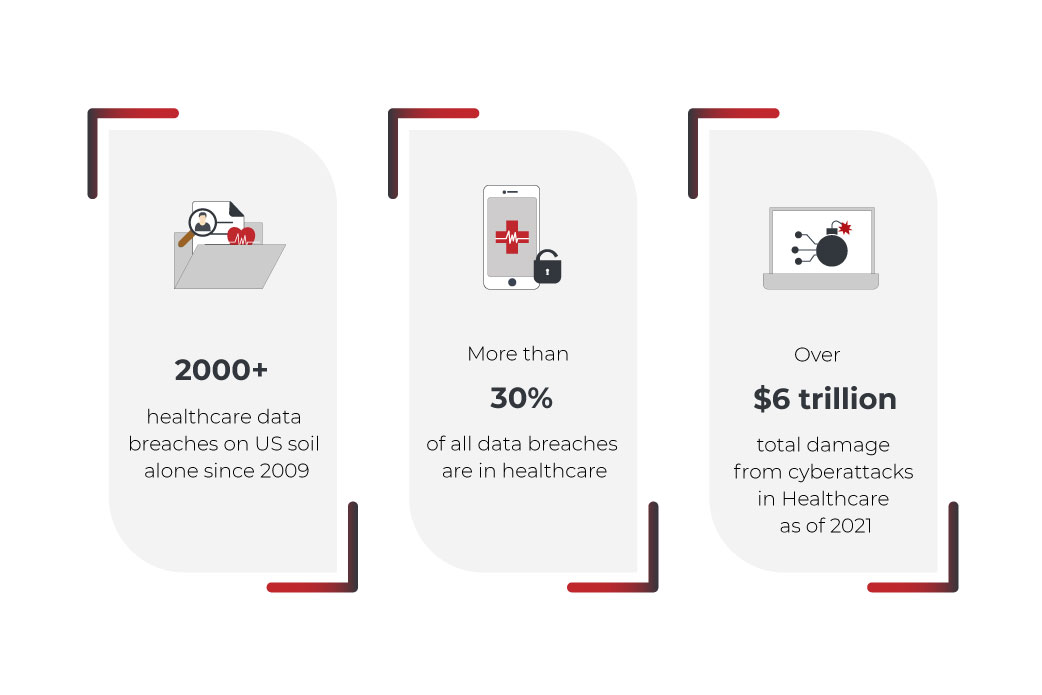
Let’s turn to healthcare cyber attacks statistics in order to better understand what a tremendous problem we are dealing with. Data leaks are just a fraction of the cyber threat that exists in the digital space. Nevertheless, even data leaks stats only can cause serious concerns in the context of the discussed issue.
According to some studies, the healthcare segment takes over more than 30% of the total data leaks cases. Since 2009, in the United States alone, there have been more than 2,000 data breaches. And although these breaches aren’t often mentioned in the lists of the largest leaks in history the trend is still troubling.
It may seem that there is a quite obvious solution to this issue – creating and implementing a reliable EHR or EMR system that has a high level of security. This is mostly true, but don’t forget that these systems are being operated by people. Besides, operating with EHR, medical specialists deal with a whole set of manual processes and actions, which, given the stress that medical workers are under (especially in connection with the COVID-19 pandemic) aren’t always done with due care. Even compliance with all HIPAA regulations doesn’t guarantee reliable storage of patient data, and the very essence of this data is a honeypot for hackers.
We provide these alarming stats in order to make people working in the healthcare industry understand that the implementation of an EMR or EHR system, as well as compliance with all healthcare cybersecurity regulations, does not maximize the security of your patients’ or customers’ data.
What types of healthcare cybersecurity threats are inherent in the healthcare industry today?
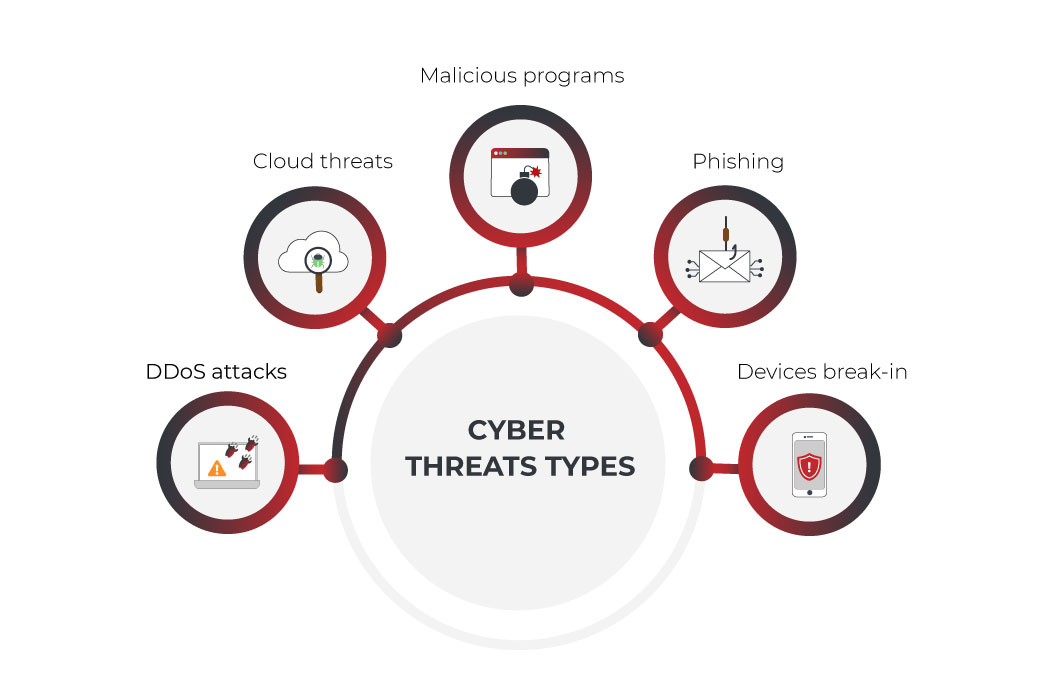
Of course, data leakage is just the tip of the iceberg. Hackers have a large number of tools and strategies and no one knows what they might come up with in the future. At this stage, the industry is experiencing security threats in healthcare systems of the following classification:
DDoS attacks
This type of cyber threat is inherent in any industry and does not cause any serious concerns, since it seems that healthcare cybersecurity companies and specialists have long learned how to deal with this problem. Nevertheless, even at the end of 2021, DDoS attacks on the servers of healthcare institutions continue, causing damage for telehealth cybersecurity. These healthcare cyber attacks are carried out in order to disrupt the servers of the product or institution for some time with a too large and intensive number of requests to the host. It should be said that this type of cyber threat is used not only by some third parties or hackers but also by competitors in a dirty struggle for the distribution of market shares.
Cloud threats
The total trend towards the cloud transition did not leave aside the healthcare industry. More and more institutions or products prefer distributed cloud storage of medical data, understandably so, since cloud solutions offer greater security and autonomy of the service. However, this trend is also evident for cybercriminals, and therefore PII and PHI data located in the Cloud space becomes a target for them. Without the proper level of encryption, such data is an easy target for criminals. Oftentimes, anything from improper Access Management to insecure APIs can become a factor in the hack’s success.
Malicious programs
This type of threat implies the penetration of fraudsters into the servers of a product or institution and the installation of a malicious program that will block the service operation. In most cases, this type of threat often develops into an attempt to extort a ransom so that the servers would be restored or stolen data would be returned. However, there are a huge number of cases when even after a successful ransom transaction, the data was not returned or returned corrupted. This is a crucial problem that raises very big concerns in any industry, especially in healthcare network security, since in the event that malware has entered the product system, there is very little opportunity to get rid of it without inflicting additional damage to the system.
Phishing
Another extremely popular and dangerous cyberattack type. Phishing is a number of techniques used to trick users into revealing their password, credit card number, and other confidential information. As you might guess, the healthcare industry contains all this data, which is why it is so attractive for phishing attacks. More often than not, attackers impersonate well-known organizations’ representatives in emails or phone calls. Phishing is extremely effective, as it relies on the low level of medical specialists’ cyber education and can skillfully lead such users into a trap.
Attacks on weakly protected devices
Finally, it should be said that the healthcare industry digitalization process implies not only the transition to the digital space but also the use of various devices, such as smartphones, which can be poorly protected. The latter is especially attractive for cyber attacks on healthcare industry, as users of mobile health applications can take unprotected actions on their devices. For example, they can visit some fraud resources with malicious programs. The next thing they know – their phone is already infected and some data from mobile health app has been stolen.
All this, as well as other, less common types of cyber threats, cause serious concerns among all people in one way or another associated with digital health. Nevertheless, while worrying about this issue won’t be superfluous, do not despair. Medical cybersecurity specialists and healthcare industry representatives work daily to minimize the chances of such attacks’ success. Some of the steps they take can be incorporated by any medical institution or healthcare product owner.
A few tips on how to improve healthcare information security
To begin with, it should be said that cybersecurity, especially in the healthcare industry, should be the subject of special attention both from the product owners or medical institutions and from ordinary users. And although even the most extreme measures still do not guarantee complete protection, implementing the following tips will significantly increase the cybersecurity of your healthcare product.
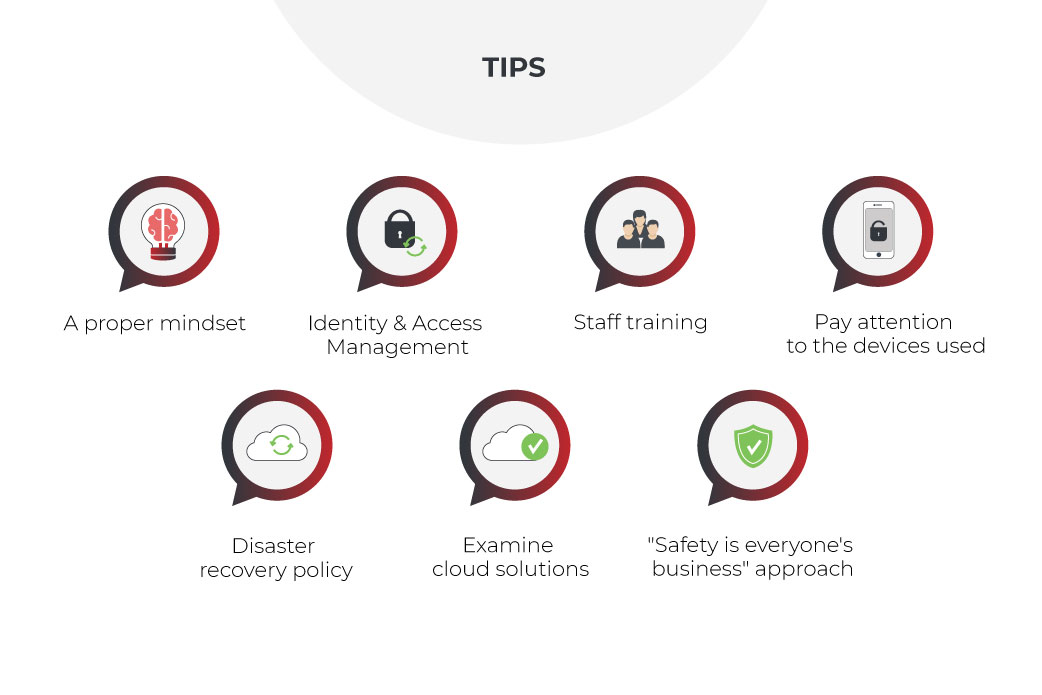
A proper mindset
First off, you need to make sure that every person, whether it is an employee of a medical institution or an ordinary developer of a healthcare product, is aware of his personal responsibility. In the context of the healthcare industry, cybersecurity is moving from the technology plane to specific people’s personal safety. Therefore, each person associated with this must understand that he is not protecting a technology or a product, he is protecting people. Any mistake made in the operation of a product or custom HIPAA-compliant CRM or EMR system will not only lead to the product harm but also inflict damage to real people. A condescending attitude to this issue and a careless approach can lead to the most serious consequences for the health and life of patients. That is why it is critically important achieving a complete understanding of responsibility among all people who are connected with the operation of the healthcare service or product in one way or another.
Identity & Access Management
Another tip is strict control over who uses the healthcare system and what data is available. Simply put, you need to make sure that only authorized people have access to certain portions of data, related to their position, role, or job title. Healthcare, like no other industry, allures external hacking, and therefore it would be good advice to establish data access only by personal and specific requests. So, let’s say a medical officer will be able to access some patient data only at his own personal request in one specific period of time and no more. At the same time, the system must have correct access tools and a clear identification method of those who request access. All these measures can be described in one term – Identity and Access management – a set of measures, habits, and tools that should be used in this regard.
DATABASE SECURITY BEST PRACTICES
Staff training
One of the most common reasons for data breaches and system intrusions is accidental improper actions by employees or app users. This issue is regulated in some way by the relevant authorities, which require employees to have an appropriate expertise level. However, regulatory compliance is not a sufficient measure. Continuous training of employees and users working with a digital healthcare product can increase the chances of cyber threat recognizing and taking preventive measures in time. Finally, such training will help to avoid simple mistakes that even the most professional specialists can make.

Pay attention to the devices used
Internet of Things (IoT) is another trend that prevails in the digital world. Today, everyone owns a large number of personal devices, be they laptops, smartphones, or smartwatches. All these devices are synchronized with each other, greatly simplifying the process of data exchange and, consequently, human life. And this very fact carries a huge threat posed by the misuse of such devices. This issue is crucial in the healthcare industry too. Every device that is used in a medical institution by employees or customers must be checked for safety. Here we’re talking not only about some kind of devices that are used by an institution or a business but also about employees’ personal devices. You shouldn’t understand this advice as a call to dig into the customers’ and employees’ personal devices. It is important to correctly spin the fact that their personal devices can become a weak link in the entire organization’s cyber defense chain. In fact, it is better to restrict access to medical data from any personal devices at all, but this isn’t always possible, since everything here depends on the specifics of the healthcare institution or product.
Disaster recovery policy
Another important factor that significantly affects the overall security of the healthcare product is the development of the correct disaster recovery policy. As we said above, one of the most popular types of cyber threats is the external hacking of the device and the malicious program installation with an extortion aim. In such situations, government agencies advise not to make any concessions to extortionists, despite the fact that the amount of the required ransom may not pose a big problem for a medical institution. The problem is that even after the ransom has been transacted, there is no guarantee that access to the data will be restored or that this action won’t be repeated in the future. The most correct solution when you’ve become a victim of such extortion is to contact the appropriate law enforcement agencies and instantly block the intruded device or data cluster with the further removal of all infected components. All these measures shouldn’t be part of the IT security team work but should be known to every employee, user or customer. This is necessary so that the very first person, faced with the intrusion, could take clear and previously agreed measures to ensure a primary protective reaction.
Examine cloud solutions
Yes, we said above that storing data in the cloud, instead of on-premise storage, does not guarantee leak-proof defense. Nevertheless, the general trend suggests that the transition to cloud storage really increases the security of storing medical data, and operational cloud backups allow you to develop a fast reaction. The best cloud vendors offer the highest levels of protection for their customers by collaborating with cybersecurity for healthcare providers, with constant proactive data backups, which also reduces the chance of a data breach. There you can also get access to tools that will help in establishing the correct Identity and Access management policy. Finally, cloud solutions lower server hosting and security costs, freeing up IT security professionals’ time for other security-related activities.
HEALTHSYNC
“Safety is everyone’s business” approach
It is important to understand that safety is the concern of every employee of the institution or user of the product. But it is also crucial to constantly declare this. At the same time, IT security in healthcare measures should be a concern not only of some dedicated IT security teams but of every employee of the company, including C-level executives. In such a situation, resources for improving security will be allocated faster and the response to any problems will be as fast and polished as possible.
Another important factor is maintaining feedback from patients (in medical institutions) and users (in healthcare digital products). Using a healthcare digital product, patients understand that they are taking risks in one way or another, and the very specificity of using such services makes them nervous. Therefore, it is critical to constantly inform your users and patients about your attention to their data security, as well as to what measures are being taken, and how important it is that they take a direct part in ensuring safety by using the product correctly.
Summing Up
The debate about cybersecurity will remain on the front pages of all news outlets for a long time, especially when it comes to the healthcare industry. The escalation rule works anytime, anywhere – as soon as security experts come up with new solutions, scammers come up with new ways to hack them. This struggle will go on forever and there is no point in trying to win, as this is impossible. What’s possible is to do everything in your power to maximize the cybersecurity of your healthcare product or institution. This is exactly what you will achieve by implementing the principles that we talked about in this article.
FAQ
Information security is critical in healthcare, as this industry stores the most valuable and personal data of patients and customers, from personal medical data to social security numbers, credit cards, and so on. In such a situation, the industry attracts a large number of fraudsters and therefore ensuring the security of storage and protection of this data is critically important.
Cyber security specialists are working to create new and improve existing solutions to ensure maximum security of digital products. However, any entrepreneur or executive can implement simple safety rules in their organization that will dramatically improve the overall level of a product or institution’s safety. We talked about what specific steps need to be taken in our article in the corresponding section. First of all, this is the creation of the correct attitude to the problem in the team, the development of a disaster recovery strategy, and a reliable and protected EMR or EHR system.
The healthcare industry is prone to a large number of fraudsters, and therefore it is inherent in almost all types of cyber threats. First of all, we can distinguish Phishing, DDoS attacks, Malware and poorly protected devices break-in.
Build your ideal
software today