Microservices Security Best Practices Breakdown


According to statistics, 81.5% of businesses use microservice-based applications, and 17.5% of them plan to adopt microservices. Roughly 9 out of 10 companies state that they are satisfied with the microservice architecture adoption.
Microservices security is strongly affected by the distinctive decoupled approach to developing apps. The inability to follow the monolithic approach needs developers to tackle new security challenges in microservices.
Below, you will learn more about the core security challenges, how to implement security in microservices, and ways to detect breaches.
What Is Microservice Architecture?
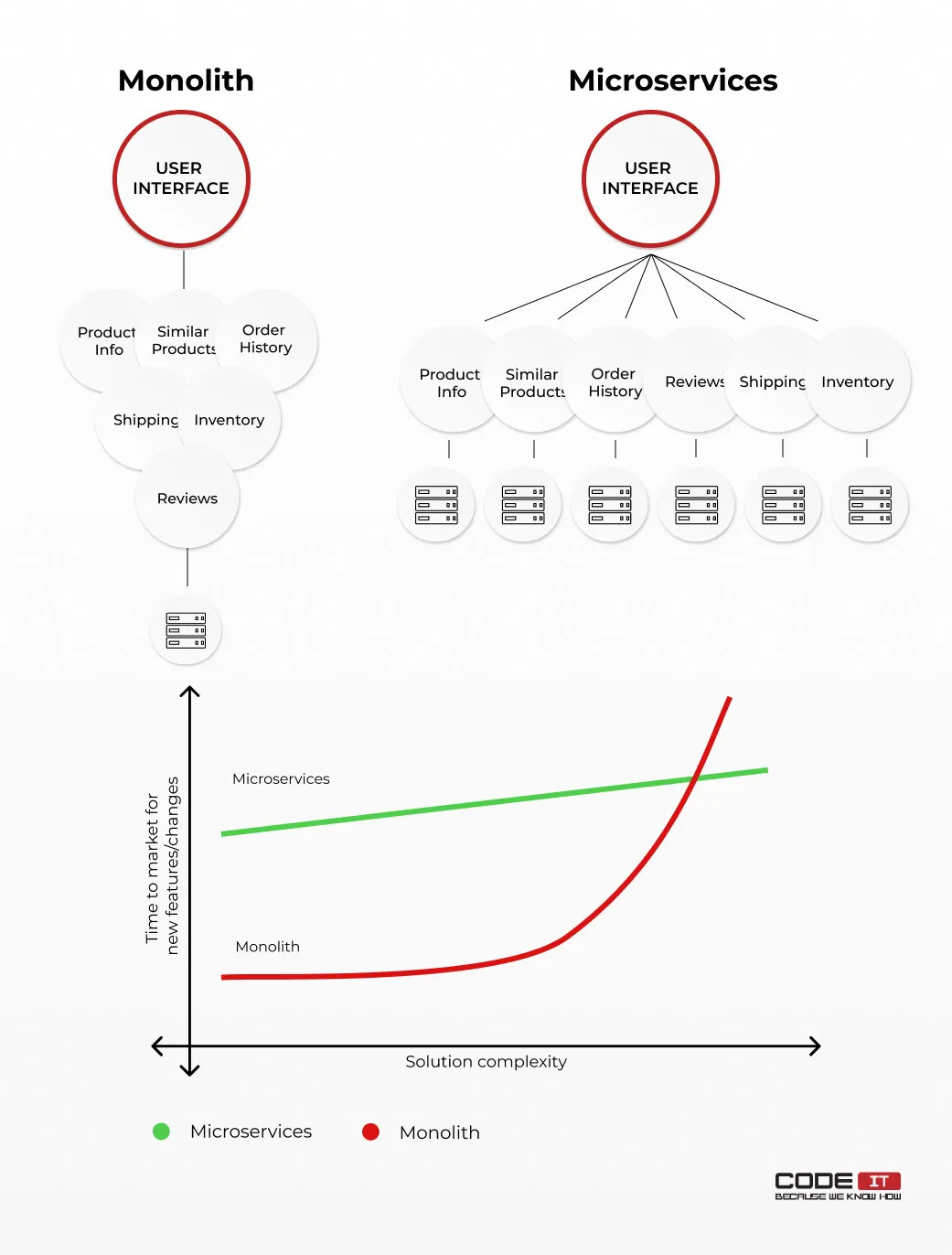
The term microservices define the decoupled architecture of an application. It comprises many loosely coupled services that use diverse technologies to deliver various functionality. Every service has a dedicated database and can be developed using diverse tech stacks.
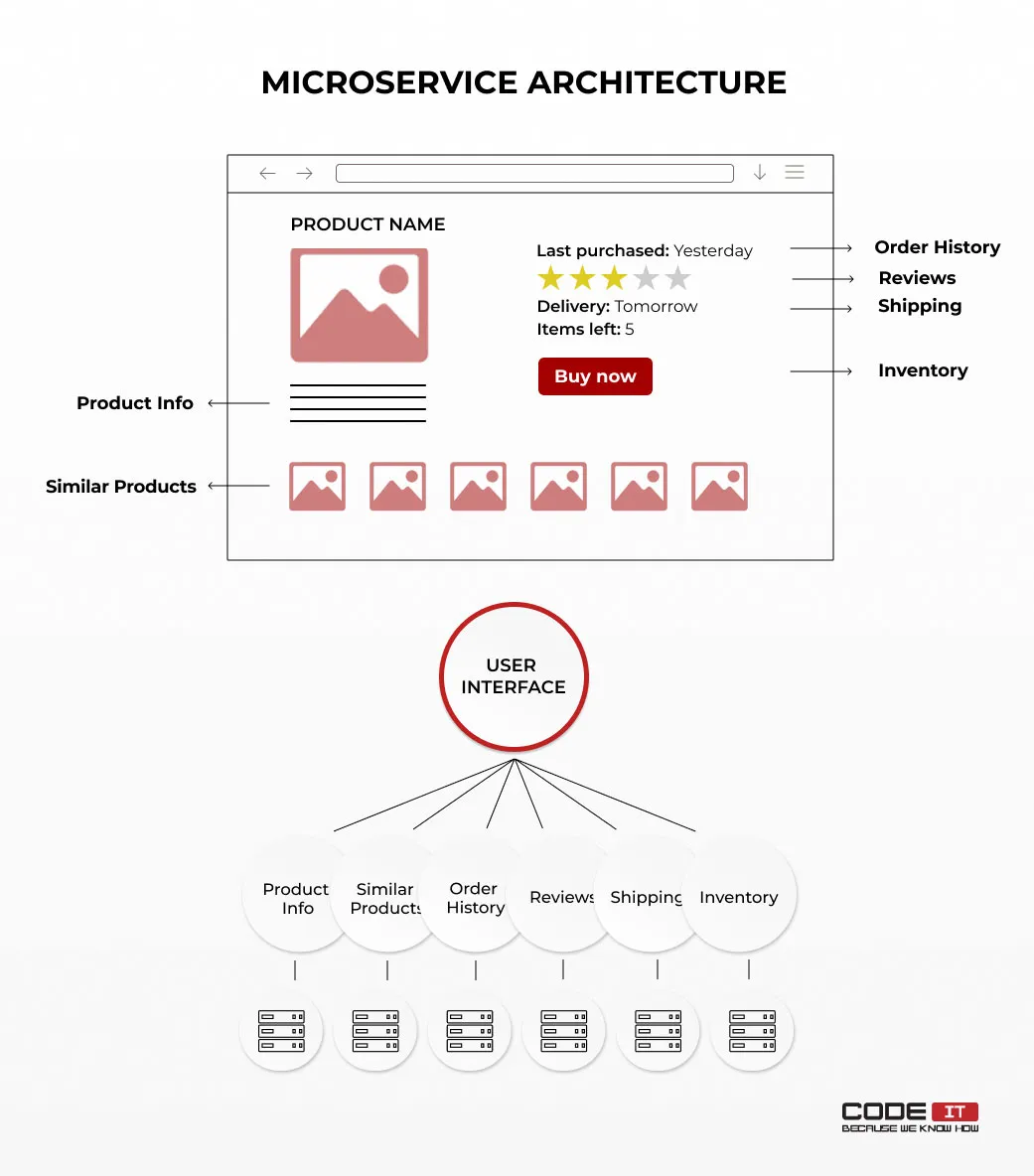
Unlike the monolithic architecture, the usage of microservices doesn’t need developers to update the entire application to add more functionality or fix detected issues. Moreover, the failure of one service doesn’t make the entire application down, which is one of the core advantages of using the microservice architecture.
What are the benefits of microservices architecture? The microservice architecture usage foresees the opportunity to create scalable and reliable applications, providing the following benefits.
- Self-sufficiency. Microservices are independent nodes that perform defined functionality.
- Technical variety. Developers can implement various solutions by using different technologies.
- Scalability. The functionality of an application can be quickly scaled up by developing and adding new services.
- High sustainability. The failure of one service does not affect the entire application, which helps enable top microservices security.
- Continuous delivery. Certain services of an application can be updated without disabling the entire app.
- Easy changes implementation. The functionality of defined services can be updated without releasing major app updates.
- Simplified onboarding. New software engineers can be quickly onboarded to a new project to start working on a new service.
Start your microservices transformation today
Business First
Code Next
Let’s talk
What are some common use cases for the microservices architecture? Considering the peculiarities of the microservice architecture, it is best suitable for the following:
- outdated applications
- large-scale applications with complex logic
- data-heavy applications
- apps that process real-time data
- highly-resilient applications
Many popular companies have switched from using the monolithic architecture to microservices to get the opportunity to scale up their apps effectively. The most popular microservices adopters are:
- Amazon
- Netflix
- Uber
Read also:
How does microservices architecture differ from monolithic architecture? In a nutshell, the monolithic architecture is a single unit that uses one database and a defined tech stack. Contrastly, the microservice app is a set of interconnected services that use diverse technologies.
Let’s elaborate on the core differences between the monolithic and microservice architectures below.
| Monolith | Microservices | |
|---|---|---|
| Scalability | The entire application should be re-deployed to release new changes or updates | New services can be deployed without affecting the entire application |
| Database | An app uses a shared database | Every service uses a database |
| Development Team | A single team of software engineers should develop, test, and maintain an app | Disparate teams are allocated to developing, testing, and maintaining services |
| Technologies | Developers are required to use a defined tech stack | Every service can be developed by using different technologies |
The monolithic architecture usage foresees the opportunity to quickly launch an app. However, the time needed to develop and release new features/changes increases exponentially, according to the complexity of an app.
The microservices architecture needs software engineers to invest a large amount of time to release the initial version of a product. The product can be easily scaled up by adding new services.
Read also:
Microservices Security Challenges And Concerns
The usage of many loosely coupled services connected into one application is a different app development approach compared to the monolithic architecture, increasing the attack surface.
The foremost microservices security challenges are mainly caused by the following:
- Decoupled architecture—every microservice uses a dedicated database and uses diverse technologies, which can lead to data consistency issues and expose access points vulnerable to unauthorized access. Moreover, the developers need to create a more complex solution to enable microservices authentication and authorization for every service, including applying security protocols and security patches regularly.
- Microservices communication—many decoupled services with dedicated functionality need to communicate and share sensitive information across distributed components, forming chains of dependencies.
Best Microservices Security Implementation Practices
Discover how to secure your microservice app by addressing the foremost microservices security challenges and implementing the best practices.
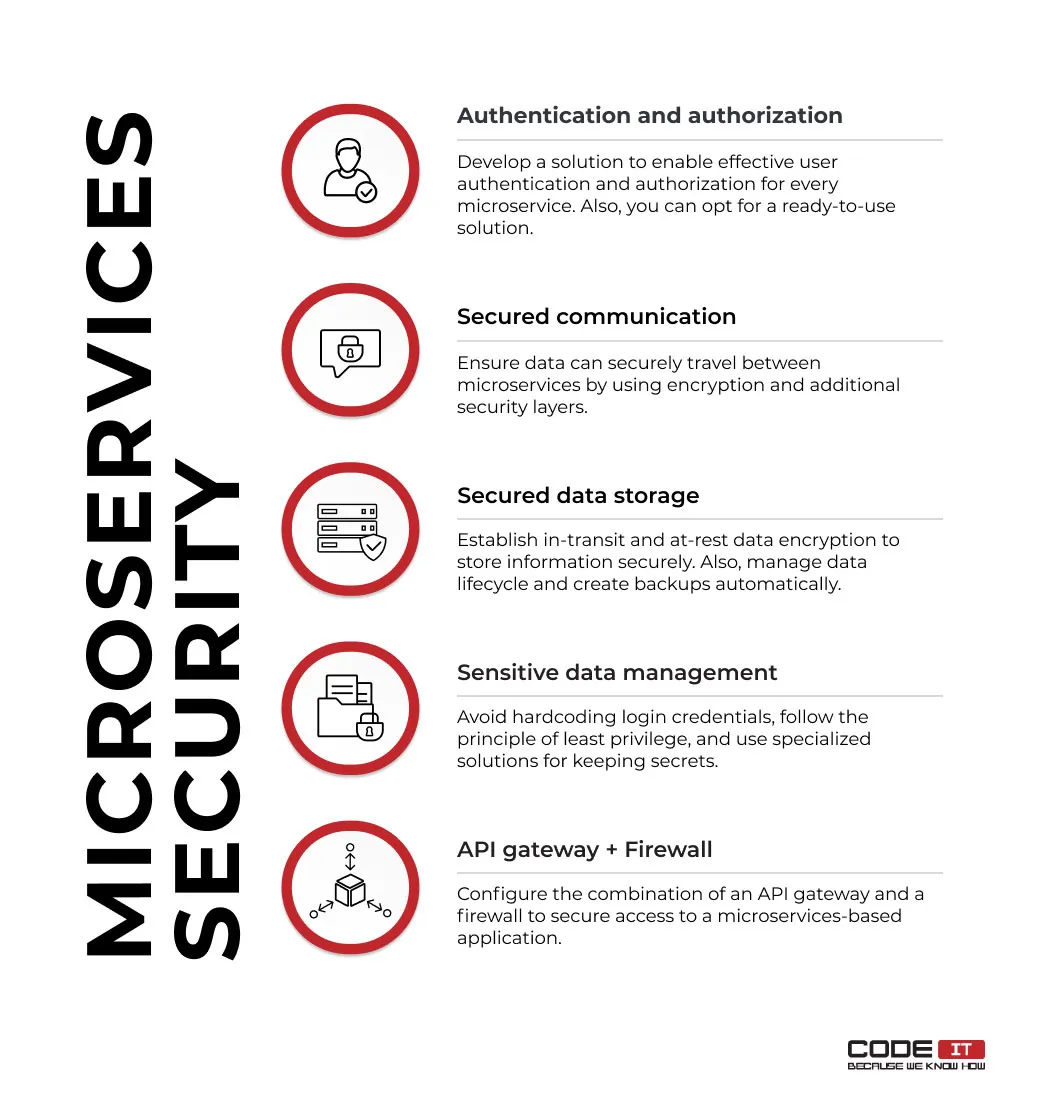
1. Authentication and Authorization
Authentication refers to the identity verification of a user by checking provided login credentials with the ones stored in a database.
Authorization refers to granting logged users permission to access defined resources. It also defines what actions users can perform, depending on their roles, in line with a security-first mindset.
A new authentication and authorization solution is needed since the microservices security architecture comprises many interconnected services. It should be different from solutions used in the monolithic architecture because every service should verify a user ID and fetch additional user info using environment variables for secure access.
Three microservices authentication and authorization implementation options
Due to the decoupled structures, the microservices security can’t follow the monolithic architecture approach. Check out the solution the monolithic architecture offers to perform core functionalities and microservices concerns.
| Monolithic Architecture | Microservices Concerns | |
|---|---|---|
| Login | Usage of a one database | A dedicated login service is required to run authentication and authorization |
| Identity Token Verification | One backend app issues and verifies ID tokens | ID tokens are issued and verified by different services |
| Additional User Info Access | All the data is stored in the same database | Data and user info are stored in different databases |
Three microservices authentication and authorization implementation options
Three options to implement secure authentication and authorization patterns in the secure microservices architecture are as follows.
- All-in-one authentication service — The authentication service verifies users’ identities and creates a session, issuing an identity token. Every service verifies tokens and gets additional user info separately in a security-aware culture.
- Shared session storage — The authentication service checks users’ identity and creates sessions that are stored in dedicated shared storage. Services verify user ID and get additional user info by connecting to the shared session storage.
- JSON web tokens (JWT) — The authentication service checks the user identity and issues a JWT token. The JWT token is provided to services, which verify it and get basic user info.
| Pros | Cons | Key Facts | |
|---|---|---|---|
| All-in-One Auth Service | Great capsulation; Basic user info is always up-to-date. | High load on the authentication service; Resource services strictly depend on the authentication service. | The best fit for microservices but a performance tradeoff should be considered. |
| Shared Session Storage | Easy to implement; No strict dependencies between authentication and resource services. | Worse encapsulation because of using a shared session storage The authentication service may become a bottleneck/point of failure; Basic user info is not up-to-date. | Great performance with a tradeoff of some microservices principles. |
| JSON Web Tokens (JWT) | No performance bottlenecks or points of failure; Promotes the decentralization approach; Basic user info can be read from a JWT. | More data to transfer over a network; JWT digital signature should be validated; Hard to implement; Not secure out of the box; Worse support in web frameworks; Revoke JWT problem. | A comprehensive option, but it can hardly handle logout. Senior developers should implement it. |
Let’s untangle the three microservices authentication and authorization options by discovering how they enable the microservices security functionality.
| All-in-One Auth service | Shared Session Storage | JSON Web Tokens (JWT) | |
|---|---|---|---|
| Login | Distinctive login API | Distinctive login API, but sessions are created in a shared storage | The authentication service creates a JWT containing user info |
| Identity Token Verification | The authentication service is called every time it is needed | Services connect the shared session storage instead of the authentication service | Services verify received tokens and get user info from them |
| Additional User Info Access | The usage of a dedicated authentication service API | The microservice authentication service API is used to fetch additional user info | Additional info can be stored in a JWT or fetched using the authentication service API upon request |
Ready-to-use customer identity and access management solutions
Regardless of a microservices authentication and authorization option you select for your microservice app, it should be implemented by software engineers.
Ready-to-use customer identity and access management (CIAM) systems can help speed up the development and address most security concerns by opting for a well-tested solution. The top-three CIAM platforms are:
Read-made CIAM solutions offer access to many features to enable top-tier security in microservices and user experience. The foremost features of the top-three CIAM platform are as follows.
| CIAM Platform | Top Features |
|---|---|
| AWS Cognito | Self-registration, Migration options, Customizable UI, Multi-factor authentication, Compromised credential protection, Microservices security risks assessment, Machine-to-machine authentication, Identity store, Access to AWS resources. |
| FusionAuth | Single sign-on, Multifactor authentication, Biometric authentication, Social and gaming logins, Breached password detection, IoT authorization, Rate limiting. |
| Auth0 | Social login, Single sign-on, Branding, Multifactor authentication, Real-time breaches detection, Serverless developer tools, Passwordless authentication. |
Fill your expertise gaps with CodeIT

Business First
Code Next
Let’s talk
2. Secured Communication Between Microservices
Microservices need to communicate with each other to send and receive data constantly. Secured communication between services is one of the pillars for enabling security in microservices. The two best practices for securing microservices communication are as follows.
Use HTTPS
Hypertext transfer protocol secure (HTTPS) is a secure protocol that enables services to communicate with each other using end-to-end encryption. Besides, it’s advisable to configure every service to validate the certificates of services they need to connect automatically, using secure configuration management tools.
Use a service mesh
The term “service mesh” defines an extra layer in a network that adds more features and improves the microservices security. A mesh network implies sidecars enabled for services, which work as proxies. The usage of a mesh network in microservices foresees the opportunity for developers to:
- simplify communication between services
- detect communication errors and failures
- encrypt and validate data
- streamline the development, penetration testing, and deployment of applications
3. Secured Data Storage
Distinctive services can be developed by using different technologies. They need to ensure that all services store data securely and minimize the chance of the exposure of services because of exploited vulnerabilities, which can be detected early via vulnerability scanning.
Check out the top three recommendations to develop secured data storage below.
Enable data encryption
The encryption of data stored in a database helps keep information safe in case of a breach because it cannot be read.
The two data encryption approaches are:
- In-transit — data is encrypted when sent from one service to another. Recipient services decrypt and read received information. It helps minimize the chance of data leakage caused by breached data communication channels.
- At-rest — data is encrypted for further storage on a hard drive. The approach helps enable additional microservices security measures when storing data and keeps it undisclosed in case of loss.
Manage data life cycle
A data lifecycle defines the amount of time data should exist in a system. Consider what data should be automatically erased, depending on the records’ creation date. This aligns with time-based security practices.
Create backups
Due to the distributed nature of the microservices architecture, the backup creation involves the configuration of every service’s database. It’s advisable to do the following.
- Conduct an audit to define crucial data that should be backed up to optimize resource usage
- Configure automatic backup creation tools as part of CI/CD pipelines
- Check the ability to restore backups error-free
- Store data backups on dedicated servers
Read also:
4. Sensitive Data Management
Sensitive data include login credentials, secrets, tokens, and keys that help grant access to users and interpret encrypted information. The top three sensitive data management practices are as follows.
Don’t hardcode login credentials
Do not embed sensitive data and login credentials directly into your application’s source code. The hardcoding can lead to serious microservices architecture security vulnerability as hackers can access secrets to obtain unauthorized access to services, especially when environment variables are not used securely.
Follow the principle of least privilege
It is one of the principles of microservices security that lies in limiting user and service access as much as possible. Defined roles should have access to only services, resources, or applications they require to perform assigned tasks, enforced via policy-enabled traffic control.
Use specialized solutions for keeping secrets
Many ready-to-use solutions can help store and manage sensitive information, including login credentials, tokens, keys, etc. Also, they offer additional functionality to enhance the microservices security architecture, including fault-tolerant and resilient designs.
The top three ready-to-use specialized solutions for keeping secrets are:
5. API Gateway + Firewall
An API gateway connects the frontend and backend. It accepts requests from users and routes them to microservices. The primary functionality of an API includes authentication, authorization, and request routing.
A firewall is an additional microservices security layer that protects networks and applications from common exploits. A firewall can filter traffic, detect suspicious activity, follow custom security rules, and integrate with CI/CD pipelines to ensure dynamic testing and deployment consistency.
An API gateway can work without a firewall. However, to enable the maximum security in microservices, it’s recommended to implement the combination of an API gateway and firewall, like:
- API gateway: AWS API Gateway + Firewall: AWS Web Application Firewall (WAF)
- API gateway: Google Cloud Load Balancer + Firewall: Google Cloud Armor
Need to enable top-tier microservice security?

Business First
Code Next
Let’s talk
Tips To Monitor And Detect Security Breaches
Continuous app monitoring helps ensure that no security issues occur and no users obtain unauthorized access, supporting incident response plans and post-incident analysis.
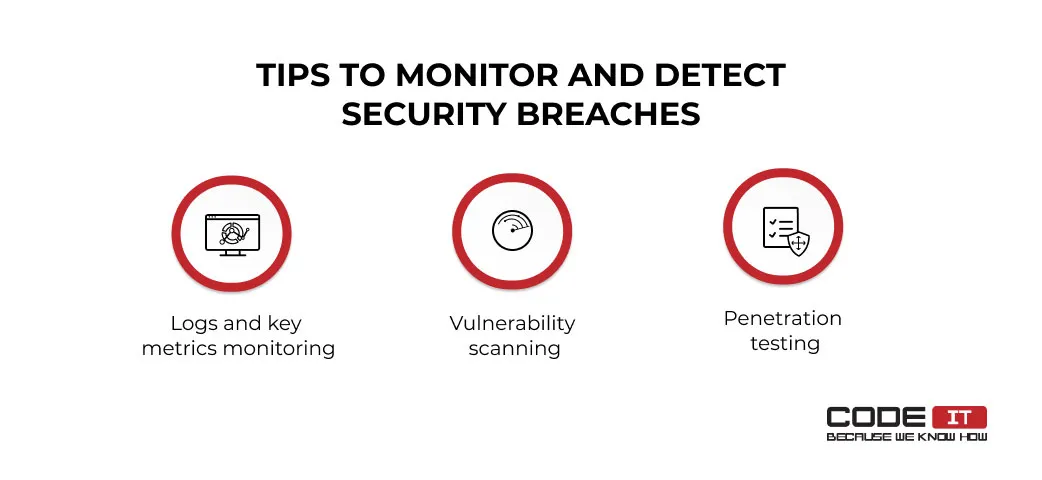
The three recommendations listed below can help detect security problems.
1. Logs and Key Metrics Monitoring
Logs monitoring is one of the basic approaches that help identify technical and security issues. It is recommended to implement a centralized log management system to monitor all the activity to detect security breaches or suspicious activity using monitoring tools and enabling security event monitoring.
Monitoring crucial metrics helps developers detect issues with security in microservices or uncommon activity. Some metrics that help define suspicious activity are:
- failed login attempts
- password reset cases
- passwordless login attempts
- user permission changes
- network traffic
- system downtime
2. Vulnerability Scanning
Possible security flaws can be detected by conducting vulnerability scans. Automated tools can analyze the codebase and detect pieces of code containing possible security vulnerabilities. Developers should further inspect the flagged pieces of code. These activities support forensic analysis as part of comprehensive incident handling. The most popular tools are:
3. Penetration Testing
In a nutshell, penetration testing is a simulation of a spear attack on an application by ethical hackers. It helps detect security exploits in advance. All the vulnerabilities detected by ethical hackers during the microservices security testing should be documented and reported to developers.
Read also:
Codeit’s Microservice Security Expertise
The CodeIT team has broad expertise in developing microservice architecture applications. Check out how we’ve built a feature-rich platform applying the microservice approach.
Problem
The client has requested the CodeIT team to develop an online service for sports fans. The project’s main idea focused on eliminating the need to use many diverse platforms by combining all the useful features in one super-app.
Solution
The app developed by our software engineer implies a lot of services that securely process large datasets and deliver rich functionality in one place. The core features of the app are as follows.
- News aggregation. The system analyzes user activity and collects the most relevant news from different sources.
- Communication platform. Users can send direct messages, create group chats, and run audio and video calls. Also, they can share screens and run public channels.
- Blockchain-driven platform. Users can exchange cryptocurrency, create smart contracts, and run blockchain-driven auctions.
- Social functionality. The application delivers advanced social media functionality, including thread and post creation. Users can make comments, reactions, and polls.
- Live streaming. Users can run live streams, share screens, and send files. Also, users can embed external resources into their live streams.
To Recap
Microservices security aims for developers to create secured applications with the minimum number of vulnerabilities.
The top microservices security best practices are:
- Authentication and authorization
- Secured communication between microservices
- Secured data storage
- Sensitive data management
- API gateway + firewall
In order to monitor and detect security branches, it’s advisable to do the following:
- monitor logs and key metrics
- scan an app to detect vulnerabilities
- conduct penetration testing
FAQ
The microservice architecture indicates the approach of building apps by connecting disparate services into one application. Every service has a distinctive database and can be developed using different technologies.
81.5% of businesses already use microservice-based applications because of many benefits that are the following:
- self-sufficiency
- technical variety
- scalability
- high sustainability
- continuous delivery
- minor changes are easier to implement
- simplified onboarding
The major microservices concerns are:
- Decoupled architecture. A new microservice authentication and authorization solution should be developed to enable every service to verify the identity of users and fetch additional data.
- Microservices communication. Services need to exchange data securely and share sensitive data.
The decoupled architecture foresees the opportunity to scale up applications rapidly. The top use case for apps developed with the microservice architecture are:
- outdated applications
- apps with complex logic
- data-heavy applications
- apps that process real-time data
- highly-resilient applications
To follow the best microservices security patterns, you need to do the following.
- Create authentication and authorization solution
- Enable secured communication between microservices
- Enable secured data storages
- Ensure secure management of sensitive data
- Use the combination of an API gateway and firewall
These pillars are applicable to any frameworks, including the spring security microservices approach.
The best options for enabling secured communication between microservices are:
- use HTTPS connection
- use a service mesh
According to the OWASP microservices security cheatsheet, it’s advisable to:
- avoid hardcoding login credentials
- follow the principle of least privilege
- use specialized solutions for keeping secrets
Build your ideal
software today